Safety and privateness are the 2 most important challenges of any trendy digitized system. Whereas information is weak through the switch from one system to a different, unauthorized entry compromises the privateness of the essential info. Therefore, the IT world is struggling to develop trendy instruments and applied sciences that add an additional layer to the present safety features. The main safety providers like Norton provide much-needed safety and the perfect mixture of Onion over VPN.

Allow us to undergo the idea of this merging of two completely different safety instruments in a single, its sensible working in safeguarding any system adopted by some fast questions on the identical. Nonetheless, earlier than leaping to mixture, allow us to perceive Onion and VPN independently.
What’s Onion?
The information within the onion community are encrypted after which transmitted by community node sequence just like the onion layers. These community nodes are known as the onion routers. The message or information arrives on the vacation spot when the ultimate layer is decrypted.

The safety of the id is at its greatest as each subsequent layer is aware of in regards to the previous layer particulars solely. Additionally it is known as the Tor community.
What’s VPN?
The Digital Non-public Community or VPN creates a easy non-public community from any public web connection.
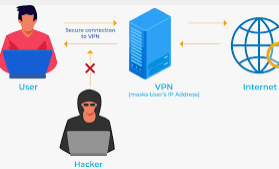
Therefore, VPNs masks the IP tackle of the web person, and all of the actions stay extremely untraceable. Subsequently, it’s good for gadgets at excessive danger of shedding information safety when linked to public web connections.
What’s Onion over VPN?
It is not uncommon and fairly understanding to want the double advantages of the onion community and VPN. Therefore, the Onion over VPN was created. Often known as Tor over VPN, this setup passes the web visitors by VPN after which by the Onion community earlier than sending it to the web servers. In different phrases, the web person’s id stays nameless, and there’s no attainable choice to hint again the connection.

It concurrently makes use of the Tor browser and VPN for any inbound or outbound information visitors. The first function of this setup is multi-layer encryption utilizing the advantages of the onion community and VPN on the similar time. Because of this, it considerably covers the double VPN advantages and affords simple use and high-end safety makes use of.
How does Onion over VPN work?
It’s simple to grasp the workflow within the Onion over the VPN community. The first wants of such setup are an excellent web connection, VPN, and onion browser. The VPN suppliers usually provide Onion over VPN setup as an in-built characteristic of their app. Allow us to perceive the inbound and outbound web information stream individually for the step-by-step working of this efficient setup.
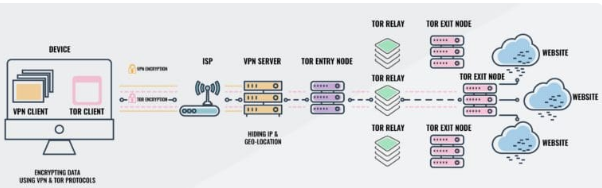
Outbound web information stream:
- The information from the machine is encrypted utilizing the VPN.
- The encrypted information from VPN is once more encrypted for including layer of encryption to the info.
- The double encrypted information is shipped to the VPN server.
- As soon as information is acquired by VPN, it decrypts the info. The onion browser or Tor browser nonetheless encrypts the info from the VPN at this stage.
- In keeping with the necessities, this encrypted information is shipped by the Tor browser to the darkish net or the clear net.
- For the darkish net, information is decrypted as soon as it reaches the vacation spot.
- For clear net, information is decrypted on the node of the onion browser after which is shipped to the World Huge Internet.
Inbound web information stream:
- The app, service supplier, or web site information is shipped to the Tor browser.
- The Tor browser receives the info and encrypts it.
- The encrypted information from the Tor community is shipped to the VPN server.
- The VPN server provides one other layer of encryption to the encrypted information from the Tor community.
- The double encrypted information is shipped to the person’s machine.
- The tor browser decrypts the info despatched to the machine.
- The VPN once more solves the info from the tor browser.
Why is Onion over VPN used?
Safety and privateness might seem to be the one two most important advantages of Onion over VPN, however there’s much more technical.
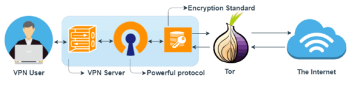
The principle benefits of this setup embody:
- It affords distinctive ranges of seamless web connectivity as VPN hides the house IP tackle and prevents it from coming into the Onion community. Therefore, the system can’t generate the IP tackle of the person.
- It affords end-to-end information encryption for the person. Even the VPN supplier can’t entry the info going to the onion community as a result of extra encryption layers over the VPN. It’s exhausting to hint again a connection made utilizing this setup. The potential for an unauthorized node within the onion community is greatest dealt with by the VPN that forestalls information entry to any outdoors entity.
- It’s an easy-to-use setup. Furthermore, a number of VPN service suppliers provide Onion over VPN setup as a built-in characteristic. Thus, it eliminates the usage of any exterior browser, and this setup is achieved utilizing a single click on solely.
- It’s attainable to entry the restricted web sites that aren’t attainable utilizing the unbiased onion community. Therefore, many customers profit from accessing darkish web sites with the mix of Onion over VPN.
FAQ:
- What’s the easy stream in Onion over VPN?
The web particulars from the machine undergo the VPN server after which move by the Onion community on this setup. After going by the Onion community, the small print attain the World Huge Internet.
- What do I would like for utilizing Onion over VPN?
The principle necessities of utilizing this setup embody high-speed web entry, a VPN, and Onion or Tor browser. Relying on the necessities, the person can go for some other browser than the Tor browser.
- How one can use Onion over VPN setup?
It’s simple to make use of this safety setup. First, the person can open the VPN app with in-built assist to this mixture. Then, as soon as a VPN connection is achieved, the Tor or Onion browser may be accessed for fast web browsing.
- Do VPNs provide in-built Onion over VPN assist?
Some VPNs like NordVPN, ProtonVPN, and so forth. comes with in-built assist to the Onion over VPN mixture. It permits fast entry to any software with out configuring it to the unbiased Onion browser.
- Is Onion over VPN completely different from VPN over Onion?
Sure, each these safety settings are fairly completely different from each other. It isn’t simple to arrange a VPN over Onion and has a unique set of benefits and functions than the helpful mixture of the Onion over VPN.
Wrapping Up:
Onion over VPN wins by giant numbers when it affords trendy safety and privateness requirements to any machine. The safety of shopping historical past from the unbiased VPN, hiding actual IP tackle, and performing all crucial duties safely is popping many VPN suppliers to supply in-built assist to this mixture. Compared with the VPN over Onion, the Onion over VPN is straightforward to setup, perceive, and comes with an extended record of safety and privateness advantages for any private or skilled person.

