Introduction
Most companies right now have gone the digital route, opening customized web sites, accessing social media platforms, and extra. One can use various software program like Avast SecureLine VPN to guard their searching expertise. Nevertheless, the opportunity of experiencing cyberattacks is excessive for many customers.
These embody varied present cyber safety points from exterior sources like malware assaults, phishing makes an attempt, and hacking. Statistically, crime complaints associated to on-line assaults have elevated at a 7% fee and better round 2020-2021. Relying on the kind of problem, one can take steps to guard towards cyberattacks. Right here, we talk about simply that!
Cyberattacks- What Does it Represent?
Cyberattacks are points that have an effect on frameworks and pc methods, damaging their common perform. It is without doubt one of the present cyber safety points that may steal, disable, or change the data/information of customers. Cyberattacks normally goal all kinds of digital platforms and connections customers use, like PCs, smartphones, inside company networks, firm computer systems, and so forth.
Listed below are the most typical forms of cyberattacks that individuals discover.
- Phishing scams– Malware enters customers’ methods by way of a corrupted hyperlink on web sites or emails.
- Malware assaults– Several types of malicious software program trigger defects in units, like viruses, ransomware, and spyware and adware.
- Service denial assaults– These contain a excessive quantity of visitors flooding that blocks servers, web sites, and community methods from regular functioning.
- Spear phishing– Superior-level phishing assaults like these goal executive-level operators in organizations and firms.
- SQL injections– These are dangerous programming codes in websites that enable community database entry.
- Password assaults– Hackers attempt to enter accounts and bypass password safety by guesswork.
A lot of these present cyber safety points can hurt the pc system efficiency, aspiring to steal information. Cybercriminals get entry to inside data, confidential information, and extra. Plus, it might probably hurt nationwide safety obtainable.
Finest Hacks for Cyber Safety that One Ought to Use
One can take a number of steps to enhance the cybersecurity of their system, digital units, or networks. We checked out lots of the proclaimed options ourselves to finalize the proper hack in totally different fields of cyber safety. Right here, you’ll study the very best options for the issues, with an in depth breakdown of the sequences.
Answer 1: Use a Password Safety Software program
One of many frequent assaults when it comes to cyber safety is stealing the password of customers. Most digital customers use a generic or simply recognizable terminology as their password. These are comparatively simpler to guess, and that reduces the power of the safety for person profiles on totally different apps.
You need to use a powerful password supervisor device like 1Password to deal with several types of passwords in a single unified area. So, households with many members or teams in corporations can retailer all passwords in a single safe location. You possibly can retailer several types of data and private credentials like login particulars, bank cards, and so forth. So, it’s the finest app you may take into account for password storage and monitoring.
This app is accessible throughout totally different working system sorts for desktop (Mac/Home windows/and so forth.), cell units (iOS/Android), and browsers (Safari, Chrome, Firefox, and so forth.).
Options:
- Customers can put together and retailer a limiteless variety of passwords.
- Limitless entry to shared vaults is obtainable.
- Customers get admin management to handle and consider various permissions.
- It’s doable to create customized teams for environment friendly teams.
- 2FA safety for passwords to guarantee optimized on-line safety.
- Duo integration advantages can be found.
Answer 2: Replace the Software program
Corporations leverage totally different functions and instruments to hold out the system capabilities to the very best restrict. The builders of third-party apps do launch new updates of the functions typically, together with superior new options, optimized interfaces, and powerful safety fixes.
If you happen to maintain the software program outdated, it can probably discover a number of errors, sluggish efficiency, and develop into extra prone to cyberattacks. So, you have to replace the apps constantly to enhance their security situations. Moreover that, if you happen to personal a tool that can’t assist the latest upgrades or future ones, it’s best to go for alternates.
Answer 3: Monitor the Privileged Customers
It is very important monitor all privileged customers from a corporation’s cybersecurity standpoint. In lots of instances, the problems that have an effect on totally different fields of cyber safety have an inside supply from the group. Customers can share the info and perform cyberattacks, so it is very important use safety software program that makes use of person exercise monitoring to detect suspicious on-line habits.
Right here, it’s endorsed to maintain related details about the monitoring course of, information assortment metrics, and so forth., safe and documented. Due to this fact, it’s simpler to entry the paperwork at a later time.
Answer 4: Safe the interior office community
In corporations and for solo entrepreneurs, WiFi networks are helpful to function usually for on-line actions. It’s helpful for quick and safe on-line searching work. Nevertheless, whereas utilizing WiFi, it’s simple for cybercriminals to breach totally different fields of cyber safety.
It’s best to use a steady VPN service like Avast SecureLine VPN. This app makes it simpler to entry public networks simply with out assaults or information loss. You possibly can anticipate an incredible pace of on-line utilization and conceal your on-line id.
Answer 5: Put together paperwork after which distribute the cybersecurity insurance policies
Particular corporations check out totally different insurance policies for cybersecurity, a lot of that are talked about right here. It might be finest if you happen to ready a technique appropriate in your firm to make use of for on-line safety. Create the doc for the method to make use of in future tasks.
Moreover, it might assist if you happen to knowledgeable the staff in regards to the new insurance policies and practices you launched. Present the policy-based paperwork to all staff and/or conduct small group-based coaching processes.
Answer 6: Replace the Safety features in your working system
Typically, the principle motive why cyberattacks are doable on methods is because of the outdated nature of the OS. It’s best to comply with the proper steps to replace the OS capabilities in your system. The steps will be totally different for particular forms of system fashions/variations.
How to do that (Home windows)?
Step 1: Go to the Begin menu and click on on it within the Taskbar. Add “Settings” within the search area and press Enter.
However, you may click on Win + I keys to open the Settings menu immediately.
Step 2: Scroll down the left pane on the menu and click on on the “Privateness & Safety” choice.
Step 3: Open Home windows Safety.
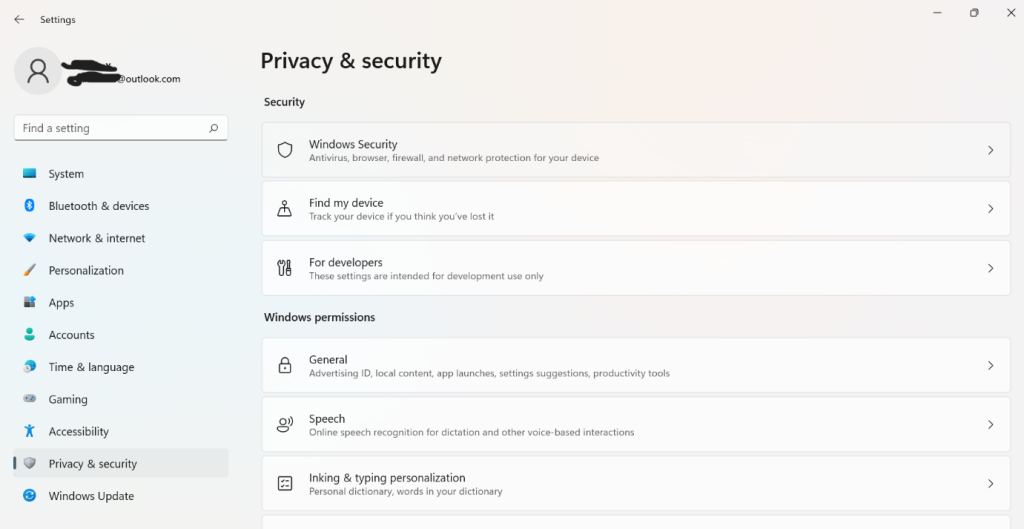
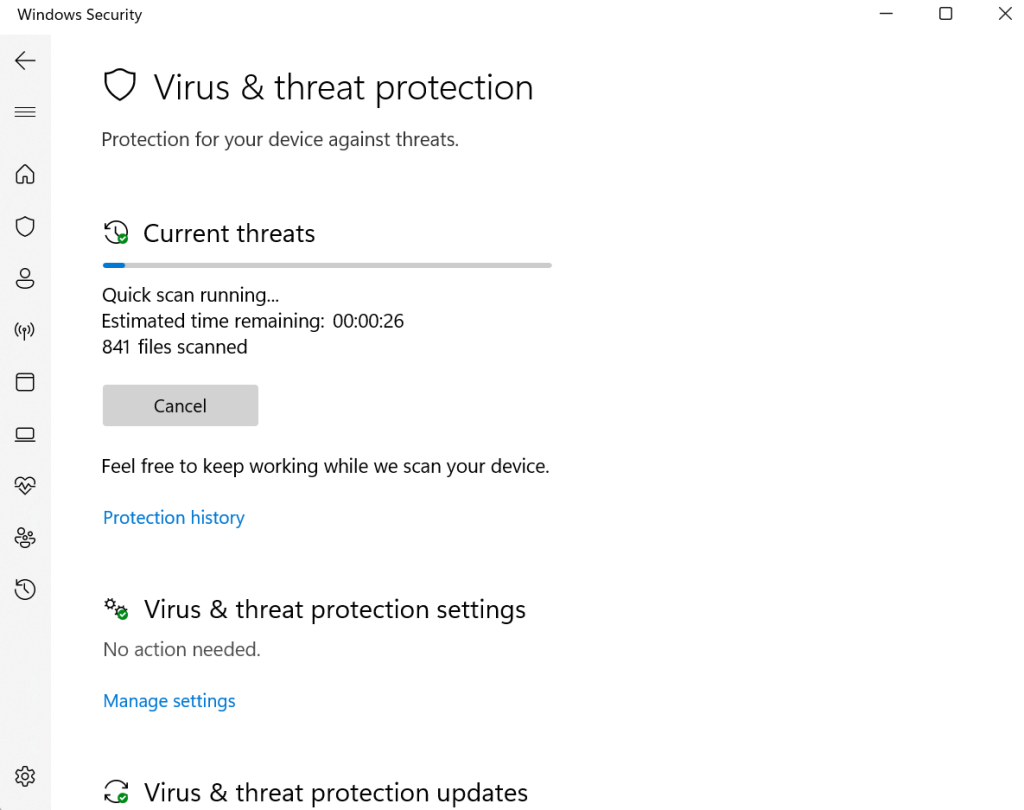
Step 4: Subsequent, select your safety setting choice like “Virus & Risk Safety” from the record.
Step 5: Beneath this window, click on on the Fast Scan button.
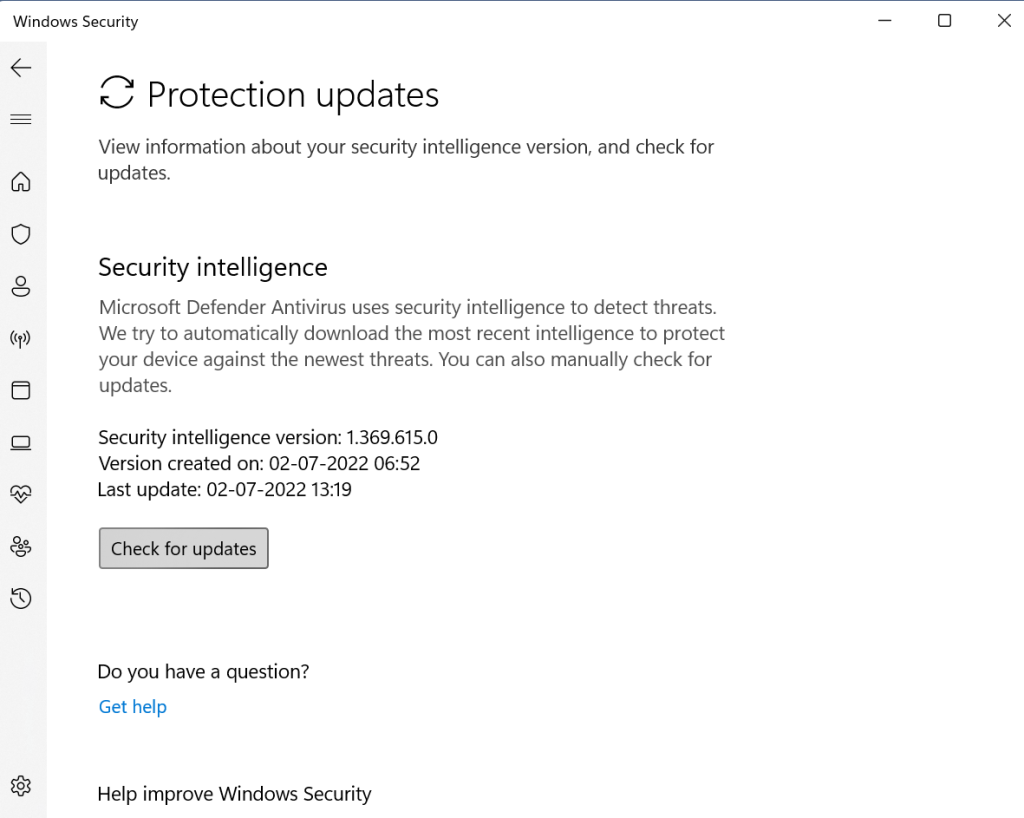
Step 6: Click on on Safety Updates > Examine for Updates > Run.
Answer 7: Set up and use an antivirus software program
Viruses, ransomware, spyware and adware, and such points are some frequent points affecting cybersecurity situations. A top-notch antivirus software program accommodates the proper options for eradicating these dangerous components from units. You need to use an choice like Avast Antivirus to guard your system and connections absolutely, browse privately, and cut back performance-based errors.
Answer 8: Use a spam filter
One of many frequent on-line cyberattacks is utilizing emails to ship malware to units. To take away these fraudulent emails out of your system, it’s best to use a spam filter to verify the emails. This spam filter software program can detect undesirable and doubtlessly dangerous emails utilizing pre-coded configurations. Then, it might take away these faulty emails and cut back potential cyber threats.
Answer 9: Again the Information
Information loss is without doubt one of the commonest outcomes of assaults in totally different fields of cyber safety. Corporations typically discover a lack of their data, which may trigger main difficulties and losses.
Therefore, it’s best to backup all information in appropriate platforms, like Cloud or an information backup and restoration software program. This works as a precautionary step to guard information from getting stolen throughout a cyber-based assault.
Why go for cyber safety hacks?
The next are the frequent causes to check out the totally different cyber safety hacks and enhance on-line security in corporations.
- Regain the misplaced belief of shoppers– Purchasers of corporations with low-standard cybersecurity would lose belief that they will shield their information.
- Unavoidable penalties– If the cybersecurity efforts usually are not up-to-date, regulation enforcement divisions can cost the model with negligence.
- Harm management– Corporations use methods to deal with present cyber safety points and breaches to keep away from any unfavorable penalties later.
- To scale back heightened cybercrime potential– Whereas developments in know-how do enable the growth of cybersecurity measures, it additionally permits cybercriminals to study new methods to assault cyber defenses.
Conclusion
All in all, these options ought to assist you handle the cyberattacks appropriately and optimize your digital security/privateness. Defend your passwords with a sturdy password supervisor, generate distinctive passwords, function cyber safety software program, and extra. Select the options to make use of primarily based on the principle points you might be coping with, and use them following the proper steps.

